NextGenXDK
Sensry and LEGIC partner to accelerate time-to-market for high-security IoT sensor applications based on LEGIC Connect
The NextGenXDK module is a working out-of-the-box kit combining hardware excellence from Sensry with mobile access control technology from LEGIC. It lets you quickly prototype / create highly secure, permission controlled IoT sensor deployments managed by standard iOS or Android devices.
IoT Sensor Kit
What is the NextGenXDK?
NextGenXDK is a groundbreaking solution that empowers rapid prototyping for a wide array of IoT applications requiring secure and managed sensor access and end-to-end data security.
The NextGenXDK is a pioneering approach to IoT sensor applications. It introduces advanced access restriction capabilities and managed encryption to guarantee only authorized sensor access while securing all data and messaging interfaces from cyberattacks. Based on over three decades of expertise in access control, the NextGenXDK leverages proven LEGIC technologies renowned for their high level of security.

Features & benefits
What is the NextGenXDK capable of?
The NextGenXDK introduces an unprecedented level of sensor access control and security which is particularly suited for business critical IoT monitoring applications in logistics, power generation, manufacturing, healthcare, finance, government, transportation, aviation, and high-security access control.
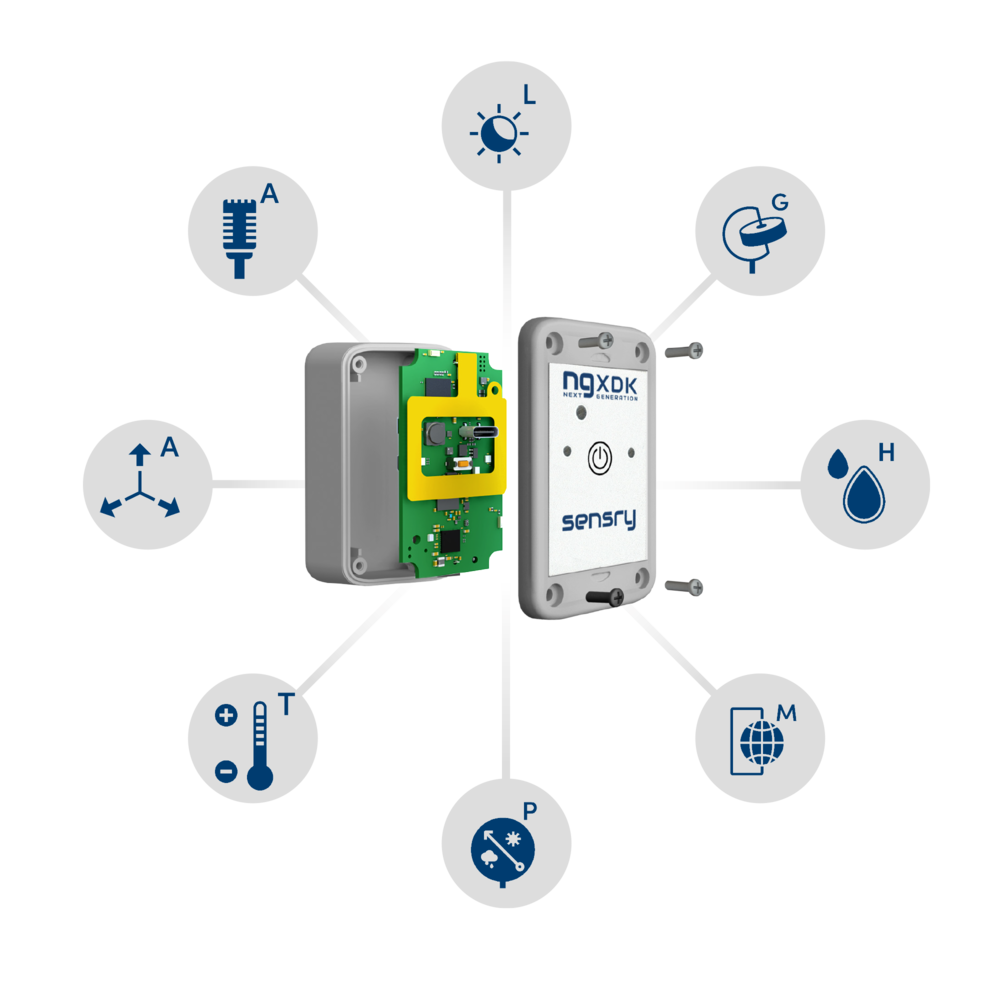
Versatility is at the core of the NextGenXDK's design, encompassing 20 different measurands, coupled with a wide array of encrypted communication options including WiFi, Bluetooth® Low Energy, ZigBee, Thread, Matter, USB, NFC, and diverse serial interfaces like RS485/ModBus.
In order to withstand industrial demands, the NextGenXDK boasts a ruggedized design including a robust, water-resistant enclosure and an industry standard M8 connector. This ensures reliability even in most challenging environments.
Customers are empowered to extend the product's capabilities through customizable firmware via the RTOS and SDK, enabling tailor-made solutions adapted to specific project requirements.
After prototype completion, purpose-built sensor modules with only required functionalities, thus size and cost optimized, can be provided by Sensry.
The product dimensions are: 71.1 x 43.2 x 26 mm
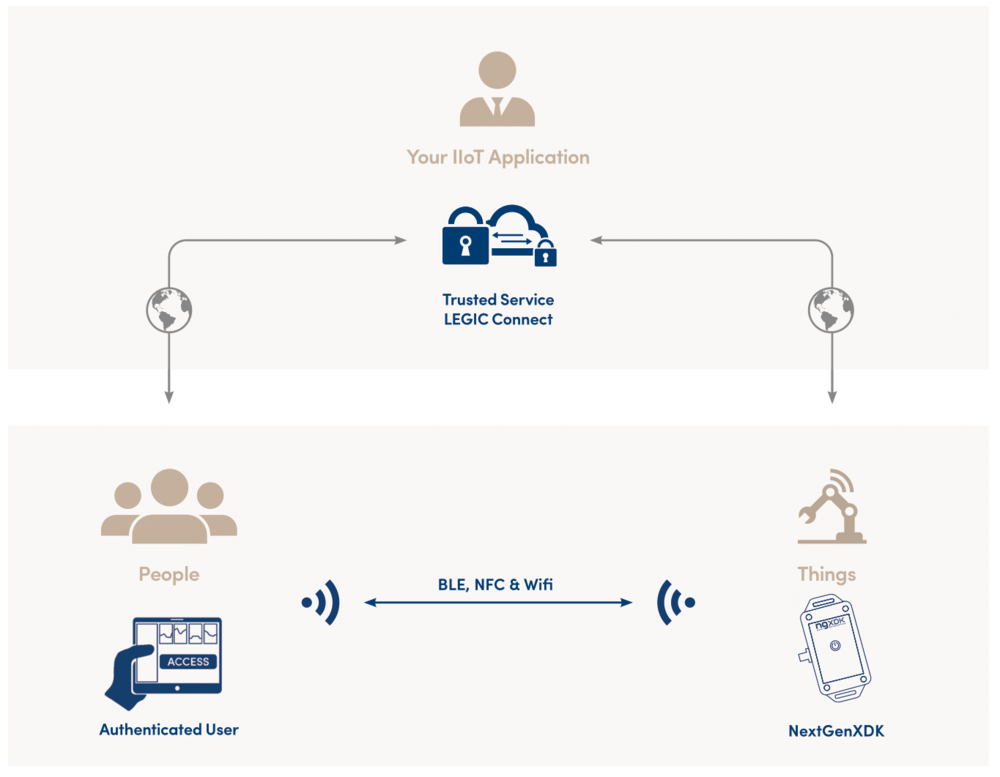
Secure Element
LEGIC Connect
With embedded LEGIC SM-6300 Security Module that communicates with LEGIC Connect Trusted Service, the sensor module prevents any attempts at unauthorized access or sensor spoofing through encryption keys stored within a secure element, ensuring data integrity and device authenticity.
NextGenXDK leverages LEGIC Connect to enable access profiles tailored to dynamically changing user roles and usage scenarios. It capitalizes on secure mobile credentialing which can be complemented with biometric identification for an added layer of access authentication.
Use Cases
NextGenXDK in action
Predictive Maintenance & Monitoring
Did you ever ask yourself, if the costly maintenance work that is done every single month is actually worth it?
With predictive Maintenance, these thoughts are history. By monitoring and analyzing a machines data, events of machine or product failure can be predicted with very high probability. Avoiding those failures allows maintenance teams to invest less resources in human resources. At the same time, maintenance teams are able to increase work productivity as they have more time to focus on vital maintenance tasks.
Benefits:
- Increased asset lifetime
- Increased ROI
- Improved productivity
- Minimize production hours lost to maintenance
- Minimize cost of spare parts and supplies
- Improved workplace safety
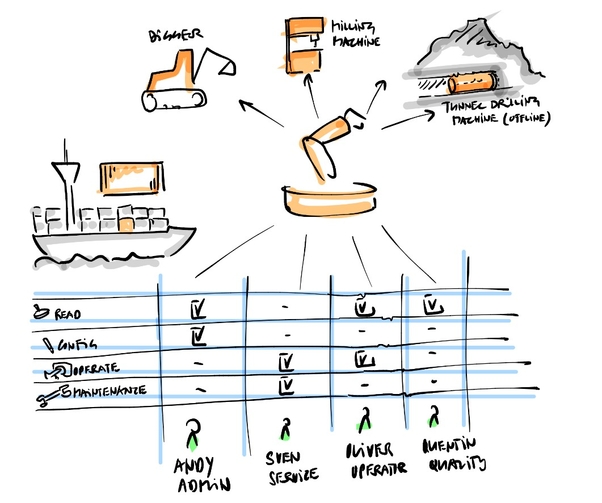
User-Specific Data Access
You need someone to use a dangerous machine to complete a task, but at the same time don’t want unauthorized people to use that machine?
You want to give a specific person access to a machines data to analyze, without giving him the rights to use the machine?
Say no more. With the NextGenXDK it is possible to create role-based or user-specific configuration. This ultimately allows you to have control over who is allowed to access what data and who is allowed to use what assets.
Benefits:
- Decide who can do what on which assets
- Improved workplace
- Precision Control
- User-Friendly
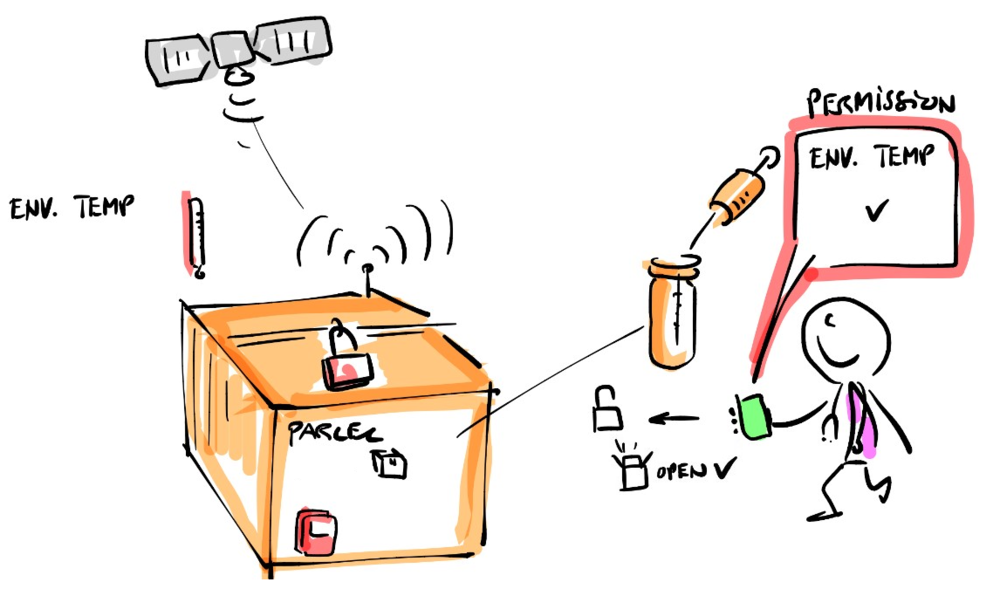
Secure Condition-Based Access
Traditionally, Legic has dedicated its efforts to fortifying access control through its credentialing technology. However, as we integrate access control with real-time environmental sensing capabilities, the need for comprehensive security transcends mere access control.
In this evolving landscape, we recognize the importance of not only safeguarding the access function but also ensuring the integrity of the condition monitoring function. This is crucial to prevent potential intruders from manipulating or falsifying environmental conditions to gain unauthorized access.
To address this critical requirement, we've seamlessly integrated Legic technology directly into our sensor systems. The result is the 'Secure Condition-Based Access' technology. This breakthrough solution empowers you to govern precisely who can access specific areas and assets while concurrently protecting the integrity of the condition monitoring function.
Benefits:
- Enhanced Security
- Intruder Deterrance
- Cost-Efficiency due to reduced security breaches, unauthorized access or safety incidents
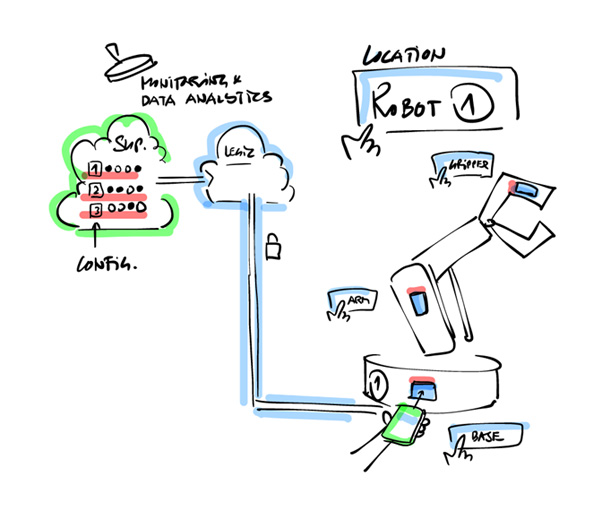
Sensor Configuration & On-Site Commissioning
Why do you need our kit to configure and commission your sensor devices?
The following scenario is still standard in many companies / industries
Bob is responsible for programming all sensors with their individual configurations. To know, which sensor is for what purpose, he packs them in individual packages to keep things tidy. Now John, the on-site worker, must be focused to place all the sensors in the right places, otherwise the use case won’t work.
The state-of-the-art commissioning contains the following sources of error:
- wrong config
- wrong information
- wrong packed
- standard or no encryption
- can be manipulated
- can be incorrectly mounted
- hard to replace at defect
- hard to reconfigure if infrastructure changes
If any of those weaknesses are met, a lot of time and money is wasted, and the work has to be done all over again.
With our kit though, you can randomly place your sensors and commission them for testing purposes with our software solution LEGIC Connect. This allows you to create your own configurations in the LEGIC Integration test environment, so that all the sensors can then be commissioned with the newly created configurations.